Puzzle given to us:
A PCAP file is given to us. Find the key to a locked pdf file inside the pdf file.
File:56C5A2B69084AEC379406CEB42CEC70C
Recommended Tools:
http://pdfcrack.sourceforge.net/
jnetpcap API
wireshark
notepad++
netbeans
Analysing the File:
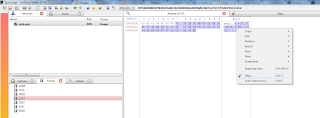
Analyzing the pcap file using wireshark will eventually leads you to realize that there are 3 pdf files in it. You may use tcp contains pdf to filter out the packets and then follow tcp stream to trace the packets flow. Next I save the data into a file and open up using notepad++. I then prune the useless data leaving only the pdf binary. Next I save the data as a pdf file.
Solving the puzzle:
After extracting the 3 pdf files from the pcap file. You will realize that 1 of them has a password on it.
There are few ways to go about breaking the password in such a short time frame
- The password is in the pcap file hidden in one of the messages
- The password is in the other 2 pdf files
- The password is a common password that is brute forceable
The best bet is to try point 3 first. We begin by running a script/program that parses packet messages into text and string tokenize them into words. These words are formed into a dictionary and passed to a pdf password cracking program to enumerate the keys and attempt to open the file. I downloaded pdf cracker and used it in a VM environment for this puzzle.
I wrote a java app in under 15 mins by grabbing online examples here and there to form this ugly duck... U may choose to rewrite it or wait for a while more for me to rewrite a proper program
import java.util.Date;
import java.util.StringTokenizer;
import java.io.*;
import org.jnetpcap.Pcap;
import org.jnetpcap.packet.PcapPacket;
import org.jnetpcap.packet.PcapPacketHandler;
import com.gargoylesoftware.htmlunit.StringWebResponse.*;
import com.gargoylesoftware.htmlunit.*;
import com.gargoylesoftware.htmlunit.html.* ;
import java.net.URL;
public class PCap {
public static void main(String[] args) {
final StringBuilder errbuf = new StringBuilder(); // For any error msgs
final String file = "300.pcap";
try {
System.out.printf("Opening file for reading: %s%n", file);
Pcap pcap = Pcap.openOffline(file, errbuf);
if (pcap == null) {
System.err.printf("Error while opening device for capture: "+ errbuf.toString());
return;
}
PcapPacketHandler<string> jpacketHandler = new PcapPacketHandler<string>() {
FileWriter fstream = new FileWriter("out.dic");
BufferedWriter out = new BufferedWriter(fstream);
public void nextPacket(PcapPacket packet, String user) {
try {
System.out.printf("Received at %s caplen=%-4d len=%-4d %s\n",new Date(packet.getCaptureHeader().timestampInMillis()),packet.getCaptureHeader().caplen(), // Length actually captured
packet.getCaptureHeader().wirelen(), // Original length
user // User supplied object
)
// convert html into text using htmlunit. I don't want html tags!
String s = packet.getUTF8String(0, packet.getTotalSize());
URL url = new URL("http://www.example.com");
StringWebResponse response = new StringWebResponse(s, url);
WebClient client = new WebClient() ;
HtmlPage page = HTMLParser.parseHtml(response, client.getCurrentWindow());
String data = page.asText();
StringTokenizer st = new StringTokenizer(data);
while (st.hasMoreTokens()) {
String token = st.nextToken();
boolean err = false;
for (int i = 0; i < token.length(); i++) {// i only want normal ascii
if (token.charAt(i) < 32 || token.charAt(i) > 126) {
err = true;
break;
}
}
if(!err)
out.write(token + "\n");
}
}catch (Exception ex) {
}
}
}
try {
pcap.loop(Pcap.LOOP_INFINITE, jpacketHandler, "jNetPcap rocks =D!");
} finally {
pcap.close();
}
} catch (Exception ex) {
}
}
}
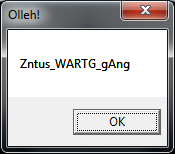
After 9000+ attempts the password to the locked file is found! woohoo... the answer to the locked file is 28-letter
Final answer: 23FB0EC48DF3EACABCA9E98E8CA24CD1 after strupr(md5('28-letter'))
Ok someone told me a 1 line solution >_<
in mac os terminal type this command strings 300.pcap | tr ' ' '\n' > 300_strings.dic
ok me noob >_<
cheers
Elucidator